Comparative Security
Sustainable levels of performance can never be achieved without keeping security at the forefront of an organization's digitalization strategy. Too often, security is treated like an after-thought - an activity at the end of the product development cycle or something to “fix” once a vulnerability is identified.
Created by:
A data-driven strategy to security
Comparative Security provides forward-leaning organizations with the information and intelligence necessary to embed security thinking as a natural part of an organization's operational strategy.
By treating security as an integral part of product development, companies can limit their security exposure, make better tradeoffs and more effectively maneuver the constant security challenges inherent in today's fast-moving business landscape.
About Comparative Security
Understand how you stack up against other companies or peers in your industry so you can more effectively target your security investments where it makes the most sense. By deploying a data-driven strategy to security, you'll be able to:
Continuous Improvement
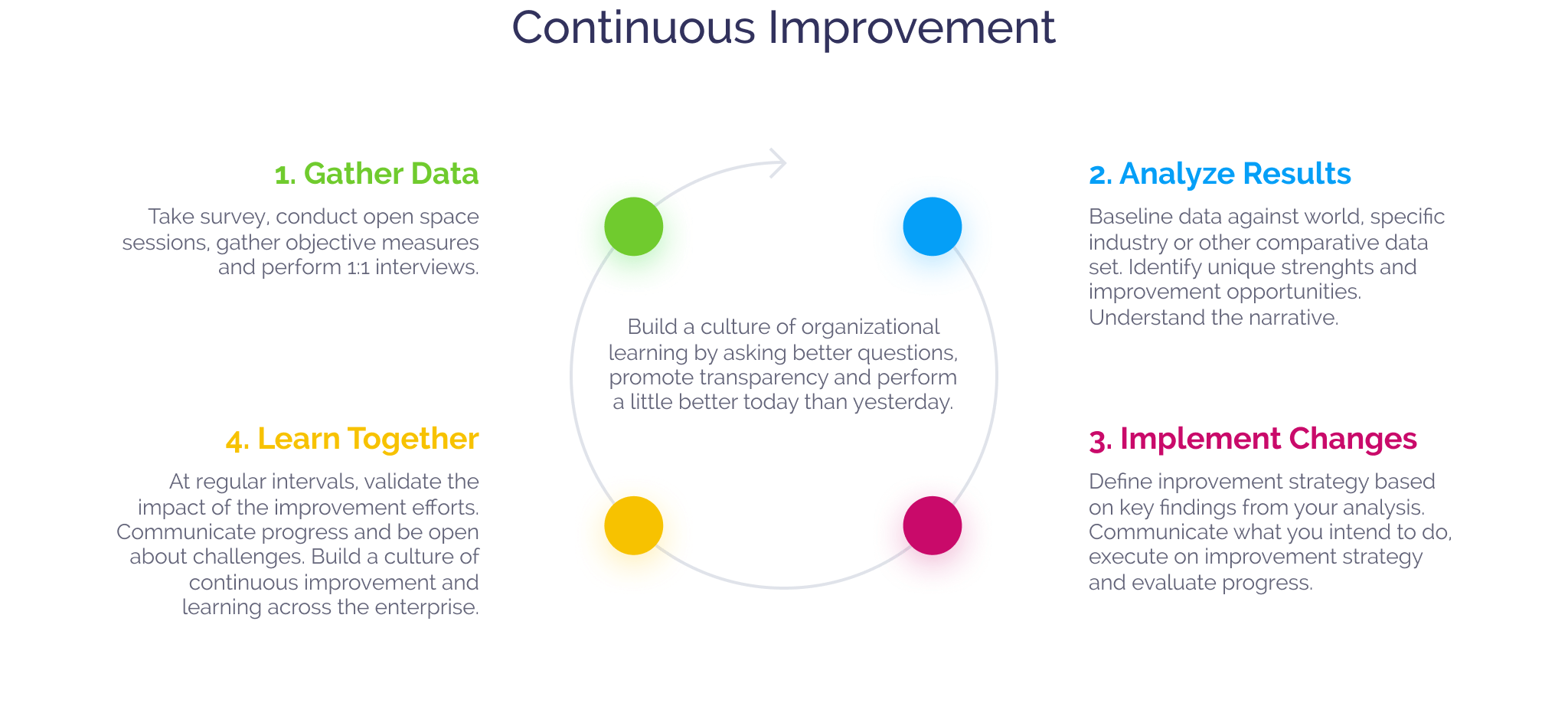
1. Gather Data
Take survey, conduct open space sessions, gather objective measures and perform 1:1 interviews.
2. Analyze Results
Baseline data against world, specific industry or other comparative data set. Identify unique strengths and improvement opportunities. Understand the narrative.
3. Implement Changes
Define inprovement strategy based on key findings from your analysis. Communicate what you intend to do, execute on improvement strategy and evaluate progress.
4. Learn Together
At regular intervals, validate the impact of the improvement efforts. Communicate progress and be open about challenges. Build a culture of continuous improvement and learning across the enterprise.
Integrate a continuous improvement approach to your security strategy: leverage Comparative Security to inform a strategic security roadmap at all levels of the organization.
Get a perspective of your current security risk profile and understand strengths and weaknesses of your approach compared to peers.
Quickly target areas of your security strategy where you need to act; recognize where you can build on existing strengths.
Give team members a voice and involve people at all levels of the organization as part of your security strategy.
Sample Questions
Governance
Our organization has an evangelist - an active advocate - who keeps stakeholders aware of the issues around information security and their importance to the business.
Intelligence
We maintain a list of open source used in apps, and have a process to keep it current with security patches.
SSDL Touchpoints
Security requirements are used to review feature designs.
Deployment
We use external penetration testers to find problems.
Outcomes
The team is producing higher quality products than before.
Governance
We have gates in our SDLC that call for security-related artifacts.
Intelligence
We analyze and document application-specific threat models and/or top attack lists.
SSDL Touchpoints
We perform basic threat modelling (perhaps with a standard questionnaire) on each new application or feature.
Deployment
Findings from penetration testing are entered into the produce development process (e.g. backlog, defect tracking).
Top Features
Embed security as an integral part of your organization's product development approach.
Benchmark your company's security efforts against peers in your industry.
Understand where you need to invest additional time and resources; amplify existing strengths.
Assess efforts at the team, program and organizational levels.